【汇总】学习VPN其实很简单
简介
包括了 gre、gre over ipsec、ipsec over gre 、ipsec vpn,附带拓扑与关键配置,可配合之前发布的模拟器做实验。
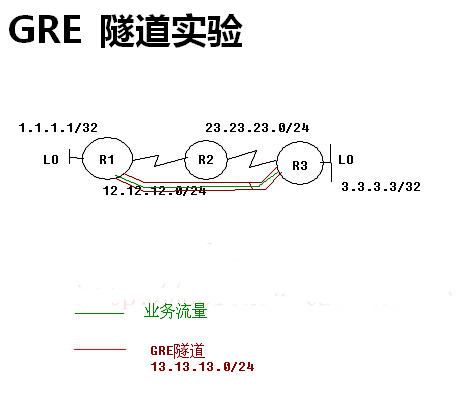
GRE隧道实验
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface Tunnel1
ip address 13.13.13.1 255.255.255.252
source Serial0/2/0
destination 23.23.23.2
keepalive 10 3
gre key ccieh3c.com
#
ip route-static 0.0.0.0 0.0.0.0 Tunnel1
ip route-static 23.23.23.0 255.255.255.0 12.12.12.2
#
interface Serial0/2/0
link-protocol ppp
ip address 12.12.12.2 255.255.255.0
#
interface Serial0/2/2
link-protocol ppp
ip address 23.23.23.1 255.255.255.0
#
interface Serial0/2/0
link-protocol ppp
ip address 23.23.23.2 255.255.255.0
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
interface Tunnel1
ip address 13.13.13.2 255.255.255.252
source Serial0/2/0
destination 12.12.12.1
keepalive 10 3
gre key ccieh3c.com
#
ip route-static 0.0.0.0 0.0.0.0 Tunnel1
ip route-static 12.12.12.0 255.255.255.0 23.23.23.1
GRE Over ipsec 隧道实验

行加密等处理,然后发送到目的端,在目的端先进行IPSEC的验证和解封装,得到GRE数据流,然后根据
本端的GRE配置进行解封装,从而得到想要的数据。
ACL的配置:因为ACL是用在IPSEC POLICY中的,因此ACL的匹配流应该是GRE封装后的数据流,根据本地
的ROUTING-TABLE找到出口IP和目的IP,据此来写ACL。值得注意的是对端的ACL要和本端的互为镜像。如
rule 0 permit ip source 1.1.1.1 0 destination 3.3.3.3 0
rule 0 permit ip source 3.3.3.3 0 destination 1.1.1.1 0
静态路由的配置:目的为TUNNEL口
IKE PEER中的REMOTE-ADDRESS为对端公网物理口的地址,因为IPSEC的对象为对端的公网物理口
应用接口:本地公网出口,因为要数据流是发往对端公网口的,也因为IPSEC的对象为对端的公网物理口
ike peer test
pre-shared-key cipher ccieh3c.com
remote-address 23.23.23.2
local-address 12.12.12.1
#
ipsec proposal pro
#
ipsec policy pol 10 isakmp
security acl 3000
ike-peer test
proposal pro
#
acl number 3000
rule 0 permit ip source 12.12.12.1 0 destination 23.23.23.2 0
#
interface Serial0/2/0
link-protocol ppp
ip address 12.12.12.1 255.255.255.0
ipsec policy pol
l
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
interface Tunnel1
ip address 13.13.13.1 255.255.255.252
source Serial0/2/0
destination 23.23.23.2
keepalive 10 3
gre key ccieh3c.com
#
ip route-static 0.0.0.0 0.0.0.0 Tunnel1
ip route-static 23.23.23.0 255.255.255.0 12.12.12.2
#
interface Serial0/2/0
link-protocol ppp
ip address 12.12.12.2 255.255.255.0
#
interface Serial0/2/1
link-protocol ppp
#
interface Serial0/2/2
link-protocol ppp
ip address 23.23.23.1 255.255.255.0
#
ike peer test
pre-shared-key cipher ccieh3c.com
remote-address 12.12.12.1
local-address 23.23.23.2
#
ipsec proposal pro
#
ipsec policy pol 10 isakmp
security acl 3000
ike-peer test
proposal pro
#
acl number 3000
rule 0 permit ip source 23.23.23.2 0 destination 12.12.12.1 0
#
interface Serial0/2/0
link-protocol ppp
ip address 23.23.23.2 255.255.255.0
ipsec policy pol
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
interface Tunnel1
ip address 13.13.13.2 255.255.255.252
source Serial0/2/0
destination 12.12.12.1
keepalive 10 3
gre key ccieh3c.com
#
ip route-static 0.0.0.0 0.0.0.0 Tunnel1
ip route-static 12.12.12.0 255.255.255.0 23.23.23.1
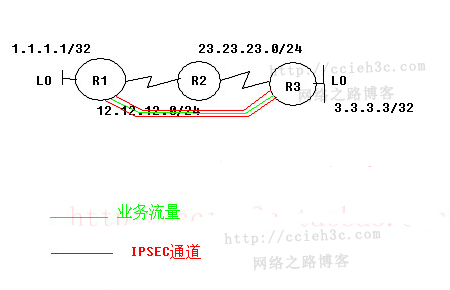
ipsec VPN 隧道实验
#
ike peer test
pre-shared-key cipher ccieh3c.com
remote-address 23.23.23.2
local-address 12.12.12.1
#
ipsec proposal pro
#
ipsec policy pol 10 isakmp
security acl 3000
ike-peer test
proposal pro
#
acl number 3000
rule 0 permit ip source 1.1.1.1 0 destination 3.3.3.3 0
#
interface Serial0/2/0
link-protocol ppp
ip address 12.12.12.1 255.255.255.0
ipsec policy pol
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
ip route-static 0.0.0.0 0.0.0.0 Serial0/2/0
ip route-static 23.23.23.0 255.255.255.0 12.12.12.2
#
interface Serial0/2/0
link-protocol ppp
ip address 12.12.12.2 255.255.255.0
#
interface Serial0/2/2
link-protocol ppp
ip address 23.23.23.1 255.255.255.0
#
ike peer test
pre-shared-key cipher ccieh3c.com
remote-address 12.12.12.1
local-address 23.23.23.2
#
ipsec proposal pro
#
ipsec policy pol 10 isakmp
security acl 3000
ike-peer test
proposal pro
#
acl number 3000
rule 0 permit ip source 3.3.3.3 0 destination 1.1.1.1 0
#
interface Serial0/2/0
link-protocol ppp
ip address 23.23.23.2 255.255.255.0
ipsec policy pol
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
ip route-static 0.0.0.0 0.0.0.0 Serial0/2/0
ip route-static 12.12.12.0 255.255.255.0 23.23.23.1
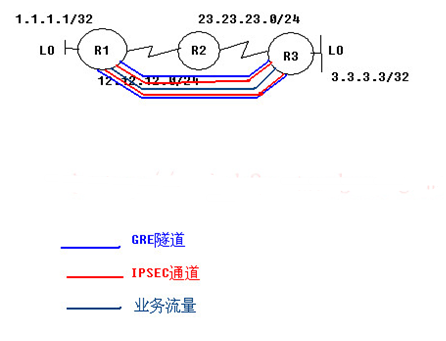
ipsec over gre
然后发送到目的端,在目的端先进行GRE解封装,得到保护数据流,然后根据本端的IPSEC配置进行验证
也解封装,从而得到想要的数据。
ACL的配置:因为ACL是用在IPSEC POLICY中的,因此ACL的匹配流应该是未经过任何处理的数据流,根据
本地的ROUTING-TABLE找到出口IP和目的IP,据此来写ACL。值得注意的是对端的ACL要和本端的互为镜像
。如rule 0 permit ip source 1.1.1.1 0 destination 3.3.3.3 0
rule 0 permit ip source 3.3.3.3 0 destination 1.1.1.1 0
静态路由的配置:目的为TUNNEL口
IKE PEER中的REMOTE-ADDRESS为对端TUNNEL的地址,因为IPSEC的对象为对端的TUNNEL口
应用接口:TUNNEL口,因为要数据流是发往TUNNEL口的,也因为IPSEC的对象为TUNNEL口
[RT1]display current-configuration
#
ike peer test
pre-shared-key cipher ccieh3c.com
remote-address 13.13.13.2
local-address 13.13.13.1
#
ipsec proposal pro
#
ipsec policy pol 10 isakmp
security acl 3000
ike-peer test
proposal pro
#
acl number 3000
rule 0 permit ip source 1.1.1.1 0 destination 3.3.3.3 0
#
interface Serial0/2/0
link-protocol ppp
ip address 12.12.12.1 255.255.255.0
#
interface LoopBack0
ip address 1.1.1.1 255.255.255.255
#
interface Tunnel1
ip address 13.13.13.1 255.255.255.252
source Serial0/2/0
destination 23.23.23.2
keepalive 10 3
ipsec policy pol
gre key ccieh3c.com
#
ip route-static 0.0.0.0 0.0.0.0 Tunnel1
ip route-static 23.23.23.0 255.255.255.0 12.12.12.2
#
#
interface Serial0/2/0
link-protocol ppp
ip address 12.12.12.2 255.255.255.0
interface Serial0/2/2
link-protocol ppp
ip address 23.23.23.1 255.255.255.0
#
[RT3]display current-configuration
#
ike peer test
pre-shared-key cipher ccieh3c.com
remote-address 13.13.13.1
local-address 13.13.13.2
#
ipsec proposal pro
#
ipsec policy pol 10 isakmp
security acl 3000
ike-peer test
proposal pro
#
acl number 3000
rule 0 permit ip source 3.3.3.3 0 destination 1.1.1.1 0
#
interface Serial0/2/0
link-protocol ppp
ip address 23.23.23.2 255.255.255.0
#
interface LoopBack0
ip address 3.3.3.3 255.255.255.255
#
interface Tunnel1
ip address 13.13.13.2 255.255.255.252
source Serial0/2/0
destination 12.12.12.1
keepalive 10 3
ipsec policy pol
gre key ccieh3c.com
#
ip route-static 0.0.0.0 0.0.0.0 Tunnel1
ip route-static 12.12.12.0 255.255.255.0 23.23.23.1
下载对应文档
关于博客资源下载说明
(1)第一种是书籍PDF与视频类,全部放在博客分享,觉得对大家学习有帮助的博主会收集好、然后以博主的经验整理分类后排序好分享出来。
(2)第二种是技术性文章与视频,全部放在公众号(网络之路博客)/B站(网络之路Blog)发布,以博主原创为主,主要分享系列为主,由浅入深的带大家了解工作中常用到的一些网络技术,当然也会分享一些比较经典的案例。
(3)分享资源有涉及到您的利益以及版权问题,请联系博主,24小时候内删除。

学习视频系列(总有您想要的)
Book与实验手册(从初级到高级)
数通系列(路由交换 无线、防火墙VPN等)
实战系列(最贴近企业需求的案例)
想第一时间收到最新更新内容吗,点击获取~~~