【汇总】多厂商防火墙系列
文档查看须知
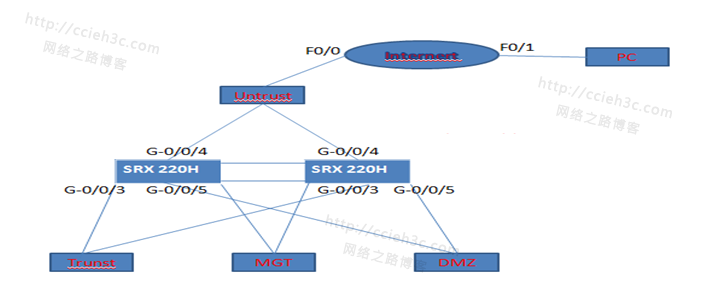
测试环境:SRX 220H两台
配置须知:SRX 220H默认带外管理口Ge-0/0/6控制口:Ge-0/0/7数据同步口:Ge-0/0/1
使用集群后则集群后接口标示为:Ge-0/0/0-7; Ge-3/0/0-7
(不同型号集群后接口显示不同,详情见官方文档)
拓扑对应IP:G-0/0/3:192.168.3.1/24
G-0/0/4:192.168.4.1/24
G-0/0/5:192.168..5.1/24
MGT:10.10.30.189-190/24
F0/0:192.168.4.2/24
F0/1:192.168.6.1/24 (模拟遥远互联网)
测试拓扑
一 Source NAT(Interface)
trust区域访问untrust源地址转换为untrust的接口IP地址;
trust区域所有主机(192.168.3.0/24)能访问untrust区域的所有服务;
配置:
set security nat source rule-set Soure-NAT-Policy from zone trust
set security nat source rule-set Soure-NAT-Policy to zone untrust
set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match source-address 192.168.3.0/24
set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match destination-address 0.0.0.0/0
set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 then source-nat interface
set security zones security-zone trust address-book address Net_192.168.3.0 192.168.3.0/24
set security policies from-zone trust to-zone untrust policy 1 match source-address Net_192.168.3.0
set security policies from-zone trust to-zone untrust policy 1 match destination-address any
set security policies from-zone trust to-zone untrust policy 1 match application any
set security policies from-zone trust to-zone untrust policy 1 then permit
set security policies from-zone trust to-zone untrust policy 1 then log session-init
set security policies from-zone trust to-zone untrust policy 1 then log session-close
验证:
Session ID: 4575, Policy name: 1/4, State: Active, Timeout: 4, Valid
In: 192.168.3.100/70 –> 192.168.6.100/40200;icmp, If: reth0.0, Pkts: 1, Bytes: 84
Out: 192.168.6.100/40200 –> 192.168.4.1/59418;icmp, If: reth1.0, Pkts: 1, Bytes: 84
Session ID: 358, Policy name: 1/4, State: Backup, Timeout: 14388, Valid
In: 192.168.3.100/58876 –> 192.168.6.100/3389;tcp, If: reth0.0, Pkts: 0, Bytes: 0
Out: 192.168.6.100/3389 –> 192.168.4.1/57479;tcp, If: reth1.0, Pkts: 0, Bytes: 0
配置解析:
set security nat source rule-set Soure-NAT-Policy from zone trust
set security nat source rule-set Soure-NAT-Policy to zone untrust
//定义NAT类型并自定义规则集名称及所应用到的源与目的ZONE(每个自定义相同名称的规则集所对应的源与目的ZONE必须一致),规则集里面
可以包含多个规则
set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match source-address 192.168.3.0/24
set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match destination-address 0.0.0.0/0
//在规则集里面定义规则,并制定规则里面配匹的源与目的地址,规则中可以直接写IP地址,也可以调用地址表的名称,调用地址表命令:set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 match source-address-name/destination-address-name
set security nat source rule-set Soure-NAT-Policy rule Source-nat-1 then source-nat interface
//关联规则集,规则,及NAT类型
set security zones security-zone trust address-book address Net_192.168.3.0 192.168.3.0/24
//定义地址表(源地址表定义必须对应ZONE(局部范围),策略里面匹配的源目的地址必须用定义的地址或地址集,不能直接使用IP地址)
set security policies from-zone trust to-zone untrust policy 1 match source-address Net_192.168.3.0
set security policies from-zone trust to-zone untrust policy 1 match destination-address any
set security policies from-zone trust to-zone untrust policy 1 match application any
set security policies from-zone trust to-zone untrust policy 1 then permit
//规则里面自定义策略名称,并按需求配置策略
set security policies from-zone trust to-zone untrust policy 1 then log session-init
set security policies from-zone trust to-zone untrust policy 1 then log session-close
//定义此条策略记录LOG
二 Source NAT(Address Pool)
trust区域内主机192.168.3.2/32,访问untrust区域所有主机源地址NAT为地址池:192.168.4.101-103
trust区域主机(192.168.3.2/32)能访问untrust区域的所有服务
配置:
set security nat source pool Source-NAT-Pool-1 address 192.168.4.101/32 to 192.168.4.103/32
set security nat proxy-arp interface reth1 address 192.168.4.101/32 to 192.168.4.103/32
set security nat source rule-set Soure-NAT-Policy from zone trust
set security nat source rule-set Soure-NAT-Policy to zone untrust
set security nat source rule-set Soure-NAT-Policy rule Source-nat-pool-1 match source-address 192.168.3.2/32
set security nat source rule-set Soure-NAT-Policy rule Source-nat-pool-1 then source-nat pool Source-NAT-Pool-1
insert security nat source rule-set Soure-NAT-Policy rule Source-nat-pool-1 before rule Source-nat-1
验证:
Session ID: 4586, Policy name: 1/4, State: Active, Timeout: 22, Valid
In: 192.168.3.2/1 –> 192.168.6.100/53517;icmp, If: reth0.0, Pkts: 1, Bytes: 84
Out: 192.168.6.100/53517 –> 192.168.4.101/35563;icmp, If: reth1.0, Pkts: 0, Bytes: 0
Session ID: 4587, Policy name: 1/4, State: Active, Timeout: 22, Valid
In: 192.168.3.2/2 –> 192.168.6.100/53517;icmp, If: reth0.0, Pkts: 1, Bytes: 84
Out: 192.168.6.100/53517 –> 192.168.4.102/62930;icmp, If: reth1.0, Pkts: 0, Bytes: 0
Session ID: 4588, Policy name: 1/4, State: Active, Timeout: 24, Valid
In: 192.168.3.2/3 –> 192.168.6.100/53517;icmp, If: reth0.0, Pkts: 1, Bytes: 84
Out: 192.168.6.100/53517 –> 192.168.4.103/53256;icmp, If: reth1.0, Pkts: 0, Bytes: 0
Session ID: 4604, Policy name: 1/4, State: Active, Timeout: 1796, Valid
In: 192.168.3.2/56233 –> 192.168.6.100/3389;tcp, If: reth0.0, Pkts: 2, Bytes: 112
Out: 192.168.6.100/3389 –> 192.168.4.101/61093;tcp, If: reth1.0, Pkts: 1, Bytes: 60
配置解析:
set security nat source pool Source-NAT-Pool-1 address 192.168.4.101/32 to 192.168.4.103/32
//定义源NAT地址池
set security nat proxy-arp interface reth1 address 192.168.4.101/32 to 192.168.4.103/32
//开启针对非接口IP地址的ARP代理,必须开启代理否则NAT转换失败!!!!!!!!!!
set security nat source rule-set Soure-NAT-Policy from zone trust
set security nat source rule-set Soure-NAT-Policy to zone untrust
//定义NAT类型并自定义规则集名称及所应用到的源与目的ZONE(每个自定义相同名称的规则集所对应的源与目的ZONE必须一致),规则集里面可以包含多个规则
set security nat source rule-set Soure-NAT-Policy rule Source-nat-pool-1 match source-address 192.168.3.2/32
//定义NAT的源地址,(目标位ANY则目标地址配置命令可以不写)这里进行NAT转换的源地址可以使用IP地址也可以使用地址表名称,如果使用定义的地址表名称则命令如下:set security nat source rule-set Soure-NAT-Policy rule Source-nat-pool-1 match source-address-name
set security nat source rule-set Soure-NAT-Policy rule Source-nat-pool-1 then source-nat pool Source-NAT-Pool-1
//关联NAT规则集,规则及NAT类型
insert security nat source rule-set Soure-NAT-Policy rule Source-nat-pool-1 before rule Source-nat-1
//调整策略的顺序
三 Destination NAT
untrust区所有机器访问192.168.4.211的21端口,NAT到DMZ区服务器FTP 192.168.5.211
untrust区所有机器访问100.1.1.212(路由可达)的所有端口,NAT到DMZ区域服务器192.168.5.212
放行untrust区到DMZ主机192.168.5.211的FTP服务,其他服务禁止;
放行untrust区到DMZ主机192.168.5.212的所有服务;
配置:
set security nat destination pool Des-Server-Ftp address 192.168.5.211/32
set security nat destination rule-set Destination-NAT-Policy from zone untrust
set security nat destination rule-set Destination-NAT-Policy rule Des-Server-ftp-1 match source-address 0.0.0.0/0
set security nat destination rule-set Destination-NAT-Policy rule Des-Server-ftp-1 match destination-address 192.168.4.211/32
set security nat destination rule-set Destination-NAT-Policy rule Des-Server-ftp-1 match destination-port 21
set security nat destination rule-set Destination-NAT-Policy rule Des-Server-ftp-1 then destination-nat pool Des-Server-Ftp
set security nat proxy-arp interface reth1 address 192.168.4.211/32
set security zones security-zone DMZ address-book address H_192.168.5.211 192.168.5.211/32
set security policies from-zone untrust to-zone DMZ policy 2 match source-address any
set security policies from-zone untrust to-zone DMZ policy 2 match destination-address H_192.168.5.211
set security policies from-zone untrust to-zone DMZ policy 2 match application junos-ftp
set security policies from-zone untrust to-zone DMZ policy 2 then permit
set security policies from-zone untrust to-zone DMZ policy 2 then log session-init
set security policies from-zone untrust to-zone DMZ policy 2 then log session-close
===============================================================================
set security nat destination pool Des-Servers-2 address 192.168.5.212/32
set security nat destination rule-set Destination-NAT-Policy from zone untrust
set security nat destination rule-set Destination-NAT-Policy rule Des-Servers-2 match source-address 0.0.0.0/0
set security nat destination rule-set Destination-NAT-Policy rule Des-Servers-2 match destination-address 100.1.1.212/32
set security nat destination rule-set Destination-NAT-Policy rule Des-Servers-2 then destination-nat pool Des-Servers-2
set security nat proxy-arp interface reth1 address 100.1.1.212/32
set security zones security-zone DMZ address-book address H_192.168.5.212 192.168.5.212/32
set security policies from-zone untrust to-zone DMZ policy 3 match source-address any
set security policies from-zone untrust to-zone DMZ policy 3 match destination-address H_192.168.5.212
set security policies from-zone untrust to-zone DMZ policy 3 match application any
set security policies from-zone untrust to-zone DMZ policy 3 then permit
set security policies from-zone untrust to-zone DMZ policy 3 then log session-init
set security policies from-zone untrust to-zone DMZ policy 3 then log session-close
验证:
Session ID: 222, Policy name: 2/6, State: Active, Timeout: 1798, Valid
In: 192.168.6.178/1075 –> 192.168.4.211/21;tcp, If: reth1.0, Pkts: 3, Bytes: 128
Out: 192.168.5.211/21 –> 192.168.6.178/1075;tcp, If: reth2.0, Pkts: 2, Bytes: 126
===============================================================================
Session ID: 296, Policy name: 3/7, State: Active, Timeout: 1764, Valid
In: 192.168.6.178/1084 –> 100.1.1.212/3389;tcp, If: reth1.0, Pkts: 2, Bytes: 88
Out: 192.168.5.212/3389 –> 192.168.6.178/1084;tcp, If: reth2.0, Pkts: 1, Bytes: 48
Session ID: 297, Policy name: 3/7, State: Active, Timeout: 1784, Valid
In: 192.168.6.178/1085 –> 100.1.1.212/21;tcp, If: reth1.0, Pkts: 7, Bytes: 313
Out: 192.168.5.212/21 –> 192.168.6.178/1085;tcp, If: reth2.0, Pkts: 4, Bytes: 259
Session ID: 298, Policy name: 3/7, State: Active, Timeout: 2, Valid
In: 192.168.6.178/3584 –> 100.1.1.212/768;icmp, If: reth1.0, Pkts: 1, Bytes: 60
Out: 192.168.5.212/768 –> 192.168.6.178/3584;icmp, If: reth2.0, Pkts: 1, Bytes: 60
配置解析:
set security nat destination pool Des-Server-Ftp address 192.168.5.211/32
//定义基于目的NAT的内网服务器地址,类似地址表的概念
set security nat destination rule-set Destination-NAT-Policy from zone untrust
//定义访问目标NAT的的来源ZONE及自定义规则集名称
set security nat destination rule-set Destination-NAT-Policy rule Des-Server-ftp-1 match source-address 0.0.0.0/0
set security nat destination rule-set Destination-NAT-Policy rule Des-Server-ftp-1 match destination-address 192.168.4.211/32
set security nat destination rule-set Destination-NAT-Policy rule Des-Server-ftp-1 match destination-port 21
//定义目标NAT的源与目的地址及端口号,源与目的地址可以直接是IP地址,也可以是自定义的地址表
set security nat destination rule-set Destination-NAT-Policy rule Des-Server-ftp-1 then destination-nat pool Des-Server-Ftp
//配置目的NAT,关联规则集,外部地址和内部地址的对应关系
set security nat proxy-arp interface reth1 address 192.168.4.211/32
//配置代理ARP,请记住,非接口IP必须启用ARP代理
set security zones security-zone DMZ address-book address H_192.168.5.211 192.168.5.211/32
//定义ZONE DMZ主机的地址表
set security policies from-zone untrust to-zone DMZ policy 2 match source-address any
set security policies from-zone untrust to-zone DMZ policy 2 match destination-address H_192.168.5.211
set security policies from-zone untrust to-zone DMZ policy 2 match application junos-ftp
set security policies from-zone untrust to-zone DMZ policy 2 then permit
//根据需求配置策略(策略中的源与目的地址必须采用地址表,不能直接使用IP地址)
set security policies from-zone untrust to-zone DMZ policy 2 then log session-init
set security policies from-zone untrust to-zone DMZ policy 2 then log session-close
//配置此条策略记录LOG
四 Static NAT
trust区域主机192.168.3.3访问地址192.168.3.5,NAT到DMZ区域主机192.168.5.3,DMZ区域机器访问192.168.3.5 NAT到trust区域主机192.168.3.3.放行任何服务;
trust区域任何主机访问192.168.111.128/25 NAT到DMZ区域服务器:192.168.5.128/25,放行服务mstsc(TCP_3389)dns(UDP_53)nsm(TCP_7800-7808) junos-icmp-all
(此配置不是常规的Static NAT,trust 区域访问DMZ区域的时候转换一切正常访问192.168.111.129 NAT到192.168.5.129依次类推,但是如果DMZ区域主动访问trust区域的机器,则第一台访问的机器的源地址转换为192.168.11.129,并非只有192.168.5.129访问trust区域的机器的源地址转换为192.168.11.129)此问题待验证!!!
配置:
set security nat static rule-set Static-NAT-Policy from zone trust
set security nat static rule-set Static-NAT-Policy rule static-nat-1 match destination-address 192.168.3.5/32
set security nat static rule-set Static-NAT-Policy rule static-nat-1 then static-nat prefix 192.168.5.3/32
set security nat proxy-arp interface reth0 address 192.168.3.5/32
set security zones security-zone trust address-book address H_192.168.3.3 192.168.3.3/32
set security zones security-zone DMZ address-book address H_192.168.5.3 192.168.5.3/32
set security policies from-zone trust to-zone DMZ policy 4 match source-address H_192.168.3.3
set security policies from-zone trust to-zone DMZ policy 4 match destination-address H_192.168.5.3
set security policies from-zone trust to-zone DMZ policy 4 match application any
set security policies from-zone trust to-zone DMZ policy 4 then permit
set security policies from-zone trust to-zone DMZ policy 4 then log session-init
set security policies from-zone trust to-zone DMZ policy 4 then log session-close
set security policies from-zone DMZ to-zone trust policy 5 match source-address H_192.168.5.3
set security policies from-zone DMZ to-zone trust policy 5 match destination-address H_192.168.3.3
set security policies from-zone DMZ to-zone trust policy 5 match application any
set security policies from-zone DMZ to-zone trust policy 5 then permit
set security policies from-zone DMZ to-zone trust policy 5 then log session-init
set security policies from-zone DMZ to-zone trust policy 5 then log session-close
===================================================================================================================
set security nat static rule-set Static-NAT-Policy from zone trust
set security nat static rule-set Static-NAT-Policy rule static-nat-Pool-1 match destination-address 192.168.111.128/25
set security nat static rule-set Static-NAT-Policy rule static-nat-Pool-1 then static-nat prefix 192.168.5.128/25
set security nat proxy-arp interface reth0 address 192.168.111.128/25
set security zones security-zone trust address-book address Net_192.168.3.0 192.168.3.0/24
set security zones security-zone DMZ address-book address Net_192.168.5.0 192.168.5.0/24
set applications application tcp_3389 protocol tcp
set applications application tcp_3389 destination-port 3389
set applications application udp_53 protocol udp
set applications application udp_53 destination-port 53
set applications application tcp_7800-7808 protocol tcp
set applications application tcp_7800-7808 destination-port 7800-7808
set applications application-set mstsc_dns_nsm_ping application tcp_3389
set applications application-set mstsc_dns_nsm_ping application udp_53
set applications application-set mstsc_dns_nsm_ping application tcp_7800-7808
set applications application-set mstsc_dns_nsm_ping application junos-icmp-all
set security policies from-zone trust to-zone DMZ policy 6 match source-address Net_192.168.3.0
set security policies from-zone trust to-zone DMZ policy 6 match destination-address Net_192.168.5.0
set security policies from-zone trust to-zone DMZ policy 6 match application mstsc_dns_nsm_ping
set security policies from-zone trust to-zone DMZ policy 6 then permit
set security policies from-zone trust to-zone DMZ policy 6 then log session-init
set security policies from-zone trust to-zone DMZ policy 6 then log session-close
验证:
Session ID: 1977, Policy name: 4/8, State: Active, Timeout: 1786, Valid
In: 192.168.3.3/52001 –> 192.168.3.5/3389;tcp, If: reth0.0, Pkts: 2, Bytes: 112
Out: 192.168.5.3/3389 –> 192.168.3.3/52001;tcp, If: reth2.0, Pkts: 1, Bytes: 64
Session ID: 1978, Policy name: 4/8, State: Active, Timeout: 1790, Valid
In: 192.168.3.3/52002 –> 192.168.3.5/21;tcp, If: reth0.0, Pkts: 3, Bytes: 140
Out: 192.168.5.3/21 –> 192.168.3.3/52002;tcp, If: reth2.0, Pkts: 2, Bytes: 126
Session ID: 1982, Policy name: 5/9, State: Active, Timeout: 2, Valid
In: 192.168.5.3/18176 –> 192.168.3.3/512;icmp, If: reth2.0, Pkts: 1, Bytes: 60
Out: 192.168.3.3/512 –> 192.168.3.5/18176;icmp, If: reth0.0, Pkts: 1, Bytes: 60
Session ID: 3723, Policy name: 7/11, State: Active, Timeout: 2, Valid
In: 192.168.5.129/21760 –> 192.168.3.129/512;icmp, If: reth2.0, Pkts: 1, Bytes: 60
Out: 192.168.3.129/512 –> 192.168.111.129/21760;icmp, If: reth0.0, Pkts: 1, Bytes: 60
Session ID: 3725, Policy name: 6/10, State: Active, Timeout: 2, Valid
In: 192.168.3.129/110 –> 192.168.111.129/1;icmp, If: reth0.0, Pkts: 1, Bytes: 60
Out: 192.168.5.129/1 –> 192.168.3.129/110;icmp, If: reth2.0, Pkts: 1, Bytes: 60
Session ID: 4010, Policy name: 6/10, State: Active, Timeout: 8, Valid
In: 192.168.3.9/60647 –> 192.168.111.129/3389;tcp, If: reth0.0, Pkts: 3, Bytes: 180
Out: 192.168.5.129/3389 –> 192.168.3.9/60647;tcp, If: reth2.0, Pkts: 0, Bytes: 0
验证上述需求括号里的内容(以下截图有误不能说明上述括号里的问题)问题待验证
Session ID: 4055, Policy name: 7/11, State: Active, Timeout: 1798, Valid
In: 192.168.5.129/1331 –> 192.168.3.9/22;tcp, If: reth2.0, Pkts: 3, Bytes: 128
Out: 192.168.3.9/22 –> 192.168.111.129/1331;tcp, If: reth0.0, Pkts: 2, Bytes: 108
配置解析:
set security nat static rule-set Static-NAT-Policy from zone trust
//定义相对那个ZONE来配置静态NAT,并自定义规则集名称
set security nat static rule-set Static-NAT-Policy rule static-nat-1 match destination-address 192.168.3.5/32
set security nat static rule-set Static-NAT-Policy rule static-nat-1 then static-nat prefix 192.168.5.3/32
//定义静态NAT的源与目的地址,并定义规则名称
set security nat proxy-arp interface reth0 address 192.168.3.5/32
//配置ARP代理。切记!!!!!!!!!!
set security zones security-zone trust address-book address H_192.168.3.3 192.168.3.3/32
set security zones security-zone DMZ address-book address H_192.168.5.3 192.168.5.3/32
//对于不同的ZONE定义对应的主机地址表(地址表针对ZONE,不是全局的概念)
set security policies from-zone trust to-zone DMZ policy 4 match source-address H_192.168.3.3
set security policies from-zone trust to-zone DMZ policy 4 match destination-address H_192.168.5.3
set security policies from-zone trust to-zone DMZ policy 4 match application any
set security policies from-zone trust to-zone DMZ policy 4 then permit
set security policies from-zone trust to-zone DMZ policy 4 then log session-init
set security policies from-zone trust to-zone DMZ policy 4 then log session-close
set security policies from-zone DMZ to-zone trust policy 5 match source-address H_192.168.5.3
set security policies from-zone DMZ to-zone trust policy 5 match destination-address H_192.168.3.3
set security policies from-zone DMZ to-zone trust policy 5 match application any
set security policies from-zone DMZ to-zone trust policy 5 then permit
set security policies from-zone DMZ to-zone trust policy 5 then log session-init
set security policies from-zone DMZ to-zone trust policy 5 then log session-close
//根据需求配置策略并记录LOG信息(策略里面的源地址与目标地址必须采用地址表的形式)
五 Source and Destination NAT
untrust所有机器访问192.168.4.100的2121端口,源地址NAT为DMZ区的接口IP,目的地址NAT到DMZ区服务器192.168.5.100;
放行FTP服务;
配置:
set security nat destination pool DMZ-ftp address 192.168.5.100/32
set security nat destination pool DMZ-ftp address port 21
set security nat destination rule-set Destination-NAT-Policy from zone untrust
set security nat destination rule-set Destination-NAT-Policy rule Des-Sour-NAT match destination-address 192.168.4.100/32
set security nat destination rule-set Destination-NAT-Policy rule Des-Sour-NAT match destination-port 2121
set security nat destination rule-set Destination-NAT-Policy rule Des-Sour-NAT then destination-nat pool DMZ-ftp
set security nat source rule-set Soure-NAT-Policy from zone untrust
set security nat source rule-set Soure-NAT-Policy to zone DMZ
set security nat source rule-set Soure-NAT-Policy rule Sour-Des-NAT match source-address 0.0.0.0/0
set security nat source rule-set Soure-NAT-Policy rule Sour-Des-NAT match destination-address 192.168.5.100/32
set security nat source rule-set Soure-NAT-Policy rule Sour-Des-NAT match destination-port 21
set security nat source rule-set Soure-NAT-Policy rule Sour-Des-NAT then source-nat interface
set security nat proxy-arp interface reth1 address 192.168.4.100/32
set security zones security-zone DMZ address-book address H_192.168.5.100 192.168.5.100/32
set security policies from-zone untrust to-zone DMZ policy 7 match source-address any
set security policies from-zone untrust to-zone DMZ policy 7 match destination-address H_192.168.5.100
set security policies from-zone untrust to-zone DMZ policy 7 match application junos-ftp
set security policies from-zone untrust to-zone DMZ policy 7 then permit
set security policies from-zone untrust to-zone DMZ policy 7 then log session-init
set security policies from-zone untrust to-zone DMZ policy 7 then log session-close
验证:
Session ID: 355, Policy name: 7/12, State: Backup, Timeout: 14406, Valid
In: 192.168.6.100/49308 –> 192.168.4.100/2121;tcp, If: reth1.0, Pkts: 0, Bytes: 0
Out: 192.168.5.100/21 –> 192.168.5.1/37932;tcp, If: reth2.0, Pkts: 0, Bytes: 0
Session ID: 4575, Policy name: 1/4, State: Active, Timeout: 4, Valid
In: 192.168.3.100/70 –> 192.168.6.100/40200;icmp, If: reth0.0, Pkts: 1, Bytes: 84
Out: 192.168.6.100/40200 –> 192.168.4.1/59418;icmp, If: reth1.0, Pkts: 1, Bytes: 84
Session ID: 358, Policy name: 1/4, State: Backup, Timeout: 14388, Valid
In: 192.168.3.100/58876 –> 192.168.6.100/3389;tcp, If: reth0.0, Pkts: 0, Bytes: 0
Out: 192.168.6.100/3389 –> 192.168.4.1/57479;tcp, If: reth1.0, Pkts: 0, Bytes: 0
配置解析:
set security nat destination pool DMZ-ftp address 192.168.5.100/32
set security nat destination pool DMZ-ftp address port 21
//定义进行目的NAT后的服务器的真实IP地址及端口号
set security nat destination rule-set Destination-NAT-Policy from zone untrust
//定义目的NAT的规则集名称及来源ZONE
set security nat destination rule-set Destination-NAT-Policy rule Des-Sour-NAT match destination-address 192.168.4.100/32
set security nat destination rule-set Destination-NAT-Policy rule Des-Sour-NAT match destination-port 2121
//定义基于目的NAT的起始(虚拟的)目地地址及端口号
set security nat destination rule-set Destination-NAT-Policy rule Des-Sour-NAT then destination-nat pool DMZ-ftp
//配置目的NAT,关联规则集,外部地址和内部地址的对应关系
set security nat proxy-arp interface reth1 address 192.168.4.100/32
//配置代理ARP
set security nat source rule-set Soure-NAT-Policy from zone untrust
set security nat source rule-set Soure-NAT-Policy to zone DMZ
set security nat source rule-set Soure-NAT-Policy rule Sour-Des-NAT match source-address 0.0.0.0/0
set security nat source rule-set Soure-NAT-Policy rule Sour-Des-NAT match destination-address 192.168.5.100/32
set security nat source rule-set Soure-NAT-Policy rule Sour-Des-NAT match destination-port 21
set security nat source rule-set Soure-NAT-Policy rule Sour-Des-NAT then source-nat interface
//配置基于源地址转换NAT地址配置
set security zones security-zone DMZ address-book address H_192.168.5.100 192.168.5.100/32
//定义DMZ区的主机地址表
set security policies from-zone untrust to-zone DMZ policy 7 match source-address any
set security policies from-zone untrust to-zone DMZ policy 7 match destination-address H_192.168.5.100
set security policies from-zone untrust to-zone DMZ policy 7 match application junos-ftp
set security policies from-zone untrust to-zone DMZ policy 7 then permit
set security policies from-zone untrust to-zone DMZ policy 7 then log session-init
set security policies from-zone untrust to-zone DMZ policy 7 then log session-close
//根据需求放行策略,并记录LOG
注意点:
2 Juniper启用已禁用的接口地址:delete interfaces ge-0/0/0 unit 0 disable;
3 Juniper调整接口的属性:
set interfaces ge-0/0/0 link-mode full-duplex
set interfaces ge-0/0/0 speed 1g
4 Juniper策略里所有的源与目的地址必须使用地址表,规则集,规则及NAT可以使用IP地址也可以使用地址表;
5 Juniper响应非接口IP的ARP请求必须手动配置代理ARP!!!!!!!;
6 关闭SYN状态检测功能:
set security flow tcp-session no-syn-check
set security flow tcp-session no-sequence-check
7 接口必须属于ZONE,否则不能与外界通讯(特殊端口除外FXP0);
8 针对不同Zone之间的策略规则名称可以相同;
下载地址
关于博客资源下载说明
(1)第一种是书籍PDF与视频类,全部放在博客分享,觉得对大家学习有帮助的博主会收集好、然后以博主的经验整理分类后排序好分享出来。
(2)第二种是技术性文章与视频,全部放在公众号(网络之路博客)/B站(网络之路Blog)发布,以博主原创为主,主要分享系列为主,由浅入深的带大家了解工作中常用到的一些网络技术,当然也会分享一些比较经典的案例。
(3)分享资源有涉及到您的利益以及版权问题,请联系博主,24小时候内删除。

学习视频系列(总有您想要的)
Book与实验手册(从初级到高级)
数通系列(路由交换 无线、防火墙VPN等)
实战系列(最贴近企业需求的案例)
想第一时间收到最新更新内容吗,点击获取~~~